I read a great deal about computer security. It is a topic that concerns me and interests me greatly. All too often the breaking news stories concern hacking and data breaches and electronic theft.
I recently read an article that suggested passwords are becoming obsolete. With the continuous advancement of processing power and speed, the time it takes for passwords to be ‘cracked’ (guessed by trial and error) decreases and the technology required to do so becomes more accessible. Future security measures will involve biometrics and/or embedded chips rather than passwords. Until then, passwords are what we have and use.
Recommended in almost every article I read about security and passwords is that passwords should be ‘strong’ (not easily guessed). In 2012, however, the three top passwords, unchanged from 2011, are still: “password”, “123456″ and ‘12345678″. Almost every article I read about passwords and security also recommend that people use different passwords for each site and account. That way, if someone does manage to obtain your password, at least they won’t be able to access all of your data or accounts. Doing so would limit the damage that could be done.
That leads to the dilemma, of course, how can one possibly remember each password for each website or account that one has?
The answer, of course, is: you can’t. To address that problem, I have seen people who use post-it notes, a journal or notebook, or even a single Word document or spreadsheet. Even a protected Office file is not very secure. Many people allow their web browser to store this information – very high risk!
I access a multitude of password protected sites. I have multiple email accounts. I have many computer log in credentials. The number of credentials I use make it impossible for me to remember them all while maintaining an acceptable level of security.
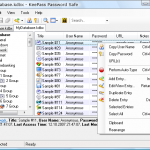
I use and recommend KeePass. KeePass is a password management database that uses an AES encrypted database for storing all of your access credentials and passwords securely. AES (Advanced Encryption Standard) is NSA approved for top secret information. KeePass is fully portable, it can be installed on and run from a USB drive. KeePass notifies you automatically of password strength. KeePass even has a random password generator built in that will make up passwords for you. In short, KeePass is an easy to use, encryption protected password management database that requires one master password for access.
Finally, KeePass is open source and, as with many of the programs I recommend, free.