If you’ve reached this page, you received my email about a recent web browsing experience that led to a mailicous attacker attempting to dupe me into installing a trojan on my PC.
Read below to follow the series of events. You’ll know how to avoid the situation yourself, should it arise.
Click any of the images below for a larger version
1) After innocently clicking a link to a desired web site, I was redirected to a url at http://extra-security-scanv.com.
The first thing that appeared was a (JavaScript) pop-up alert: “Warning!!! Your PC needs to install antimalware software! Antivir can perform fast and free scan of your computer .” [sic]
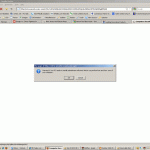
I clicked the ‘Cancel’ button, but nevertheless, was redirected to another web page.
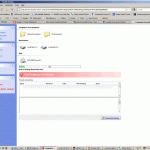
2) The subsequent page was designed to look just like a Windows (XP) Explorer Window – ‘My Computer’. Notice, however, that it appears within the browser window – in this case Firefox.
Notice the warning in red: “All information on this PC can be stolen” and the text in the red box – “Your Computer is Infected”
Looks very convincing doesn’t it?
Just look at all those problems that this scan picked up: 97 trojans in my ‘Shared Documents’ folder, 334 in ‘My Documents’, 353 on the C: drive and even 78 on the D: drive!
4) After attempting to close the tab, another JavaScript alert pops up stating: “This computer is under attack They can seriously harm your private data or files, and should be healed immediately.Return to Antvir and download it secure to your PC” [sic].
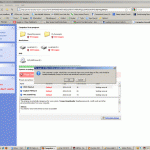
Again, I clicked cancel and was redirected to yet another page:
5) This time, mind you still caught in a craftily constructed, malicious, web page, a very authentic looking Windows Security Center window complete with a red “X” in the corner to close the window!
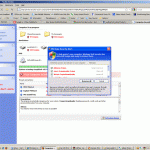
6) Now here’s the ‘gotcha’. Clicking that security center window initiates the download of Setup_2001-15.exe – the real threat.
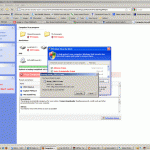
The only time my computer was in any real danger, was when the final popup prompted me to download and install the Setup_2001-15.exe file. That would have been the point of infection and that, my friends, is why this type of attack is referred to as a ‘trojan horse’. It is an attack that is meant to trick you into inviting your very foe inside your (fire)walled and protected city. In essence, I would have infected the machine myself.
At this critical point – simply cancel the download. That’s right, click the ‘Cancel’ button. In fact, if you encounter a similar scenario, keep clicking the ‘Cancel’ button, no matter how many popups appear. At the first opportune moment, close your browser window, then clear your cache (Temporary Internet Files). For those of you with experience using the ‘Task Manager’, use it to end the task.
Keep your cool. Don’t be alarmed by the ‘red alerts’, and the overwhelming number of ‘threats’ found on your computer. All you are seeing is an animated web page deceptively trying to fool you into installing malicious software.
If you have any questions about what you’ve read, or have similar experiences to share, please don’t hesitate to drop me an email.